Over the last several months, there have been many security bulletins about the vulnerabilities found in one of the fundamental technologies that makes the web work called DNS. DNS stands for domain name system. It’s a fairly complex system, but abstractly it’s fairly simple.
Every device on the Internet is accessed by Internet protocol (IP) address, which is a dotted quad like 208.67.222.222. We remember websites and services and companies by their website domain names. I’ll bet you can name the websites for Google, Amazon, eBay and AuctioneerTech off of the top of your head, but I’ll bet you don’t know what the IP addresses of the servers are that your computer talks to when you visit those sites.
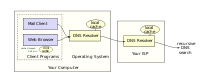
DNS exists to convert the domain names, like auctioneertech.com, into IP addresses, like 67.210.98.40. It’s like a phone book. You know the name, you need the number.
When you type the website www.auctioneertech.com into your browser, you computer first checks its cache memory to see if it has visited that site before. If it has, it further examines the record to see if that record is still valid. If it’s valid, it directs your browser to the computer at 67.210.98.40. If the TTL, or time to live, on that record has expired, the computer recognizes that the information is too old to be valid so it contacts a DNS server to find out the correct IP address of the domain. The DNS server is usually owned by your Internet service provider.
Your ISP’s DNS server has a bunch of address records in its memory, each record with its own TTL or time until expiration. Each time a subscriber requests a site it doesn’t have, it gets it and adds it to memory so it doesn’t have to get the same record again before the record expires.
The problem that’s been in the news recently relates to what is called DNS poisoning. Essentially, it’s possible to intercept the requests made by the DNS server for a domain name’s IP address and reply to them with incorrect IP addresses. For example, when the record for PayPal expires and the DNS server goes to update the record, a malicious person could catch that request and reply with an IP address for his server, causing the DNS server to tell the requesting subscriber that the IP address to PayPal is a malicious computer rather than the PayPal server. That malicious computer could serve a website that looks just like PayPal and have paypal.com in the browser address bar and the subscriber could be tricked into entering his username and password, providing access to his bank account to the malicious person. This attack is not Paypal’s fault, it’s the fault of the original DNS technology which was far too trusting.
Recently, patches and updates have been made to many DNS servers from many different ISPs. The problem is that you may not know if your provider has updated its servers. There is a test located at DoxPara to tell if your DNS is vulnerable to the latest attacks, but the far better choice in my opinion is to use OpenDNS.
OpenDNS is a distributed network of free DNS servers that are faster and more secure than your ISP’s DNS server. Because they have so many users, the odds of them having the website you’re looking for are much higher, allowing them to return the IP address immediately rather than having to look it up. They’re on top of their game, which means you can always trust that they’re running the latest updates and patches.
They have a fantastic control panel which not only provides statistics showing total requests, unique domains, unique IPs and more, they will allow you to block categories of websites or specific domains or IP addresses. You can block dating sites, gambling sites, auction sites, adult sites, gaming sites, religious sites, blogs – the list goes on. If you’re an auctioneer, you probably want to allow auction sites but block adult sites. If you’re a school, you probably want to block dating sites and religious sites as well. OpenDNS lets you block these categories and more. I have music sites blocked, but my staff likes to listen to Pandora Internet radio, so I can block the music category but specifically allow Pandora.
OpenDNS automatically blocks known phishing sites, which means that if you try to visit a site that is known to be malicious or to try to extract personal information from you, it will block it until you specifically allow that site in the OpenDNS control panel.
If you manage a network, simply enter the free OpenDNS server addresses in the configuration of your router and rest assured knowing that your router will cause all the computers on your network to go through the OpenDNS servers. If you manage multiple networks, the OpenDNS control panel will allow you to block and allow specific website categories for each network or all at once. If you have a notebook computer and are accessing the Internet at a wireless hotspot, you can use the OpenDNS servers specifically on your notebook to ensure that you’re really going to the sites you wanted to go to rather than hoping that the DNS servers used by the hotspot are not vulnerable or already poisoned.
One final feature is intelligent redirection. If you type example.cm on a normal DNS server, it will take you to either a page not found 404 error or a scam site or ad site hosted by a domain squatter. Type example.cm on a computer using OpenDNS and it will recognize that you probably meant example.com and correctly take you to the site you meant to visit.
How can OpenDNS provide such a fantastic service for free? When you enter a site like example.cm and it doesn’t have a good guess as to what you really meant, it will display a page of Google-powered search results as if you entered that website into the search bar rather than the address bar. OpenDNS takes a percentage of the ad revenue generated if you end up clicking on one of the sponsored links. You can customize the logo using the OpenDNS control panel so that it looks like search results from your company, which is a particularly nice feature if you manage a network. The address bar search is so nice that I’ve found myself getting lazy and entering everything in the address bar because I know that OpenDNS will cover for me and convert the malformed website address into a search query.
With all the baddies on the Interwebs, OpenDNS provides peace of mind that when you type an Internet address in the browser’s address bar you’ll end up where you wanted. It provides an increase in browsing speed which translates to an increase in productivity. It makes you safe and boosts your bottom line. And it’s absolutely free.
Start using OpenDNS today. You don’t even have to go to their website. Simply enter these two DNS server addresses into your router or the network properties of your computer.
208.67.222.222
208.67.220.220
If you entered those without verifying that they’re correct, shame on you. Trust no one when it comes to this kind of security, not even me. You can go to www.opendns.com and scroll to the bottom where the addresses are displayed to verify that they’re correct (which they are). Then you should enter the addresses in place of the DNS provided by your ISP to start using OpenDNS.

By John 14 October 2008 - 8:03 am
Excellent tip! I have used OpenDNS on my laptops for sometime, and am always impressed with the speed. Now that you mention it, I should switch our routers in the office over. I wonder how this would work with a mail server?
Thanks again for the great article!
By Aaron 14 October 2008 - 8:20 am
@John –
It shouldn’t affect anything. A mail server needs to be public in order to work. If it’s public, it must make its DNS records available to everyone, including OpenDNS. Let us know if it causes you problems, but my guess is that it won’t.
By Aaron Traffas 14 October 2008 - 1:20 pm
@John –
It shouldn’t affect anything. A mail server needs to be public in order to work. If it’s public, it must make its DNS records available to everyone, including OpenDNS. Let us know if it causes you problems, but my guess is that it won’t.
By John 14 October 2008 - 1:03 pm
Excellent tip! I have used OpenDNS on my laptops for sometime, and am always impressed with the speed. Now that you mention it, I should switch our routers in the office over. I wonder how this would work with a mail server?
Thanks again for the great article!
By Subdomains and multiple web hosts | AuctioneerTech 13 March 2010 - 10:54 am
[…] mentioned subdomains in our recent series about branding. We’ve discussed DNS before, but we’ve never looked directly at subdomains and how they can help us as auctioneers […]
By DNSCog reports on your website’s domain name servers | AuctioneerTech 20 May 2010 - 8:03 am
[…] a single website across multiple servers and even multiple web hosting providers. We’ve discussed DNS before, and it was even the co-subject of the Auction Podcast episode 8, but in a nutshell DNS is the […]